Over the weekend, I’ve been trying to call Powershell scripts using vRealize Orchestrator.
Quick google yielded the following:
http://blogs.vmware.com/orchestrator/2011/12/vco-powershell-plug-in.html
I’ve followed the blog and was able to successfully call the script WITH one exception: every time i started calling resource outside of the WINRM host from the ps script – it kept on failing. One example is – Adding DNS which required to call the Domain controller.
Another google and found this AWESOME article from Spas:
http://kaloferov.com/blog/using-credssp-with-the-vco-powershell-plugin/
TLDR:
Basically, you need to use CredSSP to impersonate calls. Since vRO, currently, does not support this – you need to configure the WinRM server to allow CredSSP/ Impersonation and call the script using CredSSP.
The following items needs to be enabled in the WinRM Host:
Go to gpedit.msc -> Choose Enabled for the items and add the following in the allowed servers: WSMAN/*.<your domain>

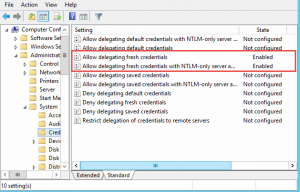




That leaves a bit of a security loophole, but is clearly the simplest method.
I have gotten around this slightly differently – I have set up an SSH server on the Windows box that I use as a Powershell host and use SSH to hit the Windows box and kick off locally hosted Powershell scripts.
Since they are executed locally, they don;t suffer from the 2 Hop security issue found when bouncing through WinRM Hosts.
Sadly, it is not prettier than a blanket enabling of the policy above (and I have to handle code execution and credentials on the Powershell host)