Since last week, I’ve been running harbor using a self-signed certificate. This is okay for home-lab purpose but annoying once you start integrating with Kubernetes. This is because you need to modify the each node to trust the self-signed cert to be able to push/pull images, and with TKG providing scale-out k8s installation – this is a headache to integrate.
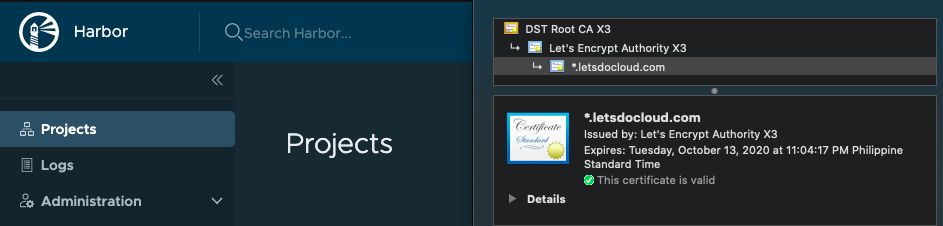
To solve this, we can use LetsEncrypt to provide the free certificates and bring it into harbor installation. Ideally, the certificate needs to be a wildcard as to provide flexibility in applying into my installation.
There are multiple ways to achieve this (i.e, using certbot) but I prefer to re-use what I have right now which is:
- Traefik (v2.2) running and dumping acme.json for *.letsdocloud.com
- You need to configure this with DNS hand-shake
Now, to extract the certificate from acme.json, I’ve forked an open-source python script to adopt the new Traefik 2.2 – acme.json format. The other open-source projects available was just not working for wildcard or letsencrypt or traefik v2.2.
Here’s the modified code – I’ve done:
https://gist.github.com/dmnt3d/a9696d1590df0a1410be8954df15f59c
Once you have the acme.json and the above script, perform the following:
- Execute the script
python3 extract.py acme.json *.letsdocloud.com dump/
- This will generate two files. Rename them to the following
- fullchain.pem = tls.crt
- privkey.pem = tls.key
- Create kubernetes secret
kubectl create secret generic sslcerts --from-file=tls.crt --from-file=tls.key -n harbor
- Modify values.yaml of the harbor helmchart to reflect the secret name
tls:
enabled: true
secretName: "sslcerts"
- Install using Helm …and enjoy!





We picked up a lot, ATP.