For this post, I’ll document how to setup Harbor registry using Traefik as an ingress controller with a valid certificate from LetsEncrypt . Documentation around the topic is scattered in different places and people just assumes you’ll figure out the trivial details. So without further ado… let’s start with a quick pre-requisites.
Pre-requisite
As an image registry, Harbor needs to have a valid certificate for it to be trusted endpoint when pushing images. Otherwise, you need to manually trust the insecure certificate to be able to interact with it. In a kubernetes cluster this is especially painful given the capabilities to scale-in/out the nodes like what Tanzu Kubernetes offers. Luckily, there are options to get around this which does not cost an arm and a leg.
DISCLAIMER: The following are my personal way of doing it. Vendors and configurations are of my personal preference. There are multiple ways to skin a cat… this is just one of them 🙂
What we need to get started
- Public Domain Name
- We will be using this as the domain for our harbor registry.
- This will set you up around 3-5$ per year depending on how complex the domain is.
- Cloudflare managed Domain Name
- This is a free service.
- CloudFlare is chosen as it will be used to validate LetsEncrypt handshake for issuance of the trusted certificate.
Setting up Cert-Manager with Cloudflare
The following assumes you already have cert-manager running in your kubernetes cluster. In case you need you to install, cert-manager has an awesome documentation you can follow.
Installation steps: https://cert-manager.io/docs/installation/
After installing cert-manager, we need the following high-level steps:
- Manage your domain name with Cloudflare
- Create an API key from Cloudflare that allows us to call/create DNS resource.
- DNS handshake from Cloudflare to LE removes dependency on the connectivity of our on-premise setup. The only requirement for this setup to work is to have cert-manager out-bound call to cloudflare API to create the TXT resource and LE to request cert.
- Create a secret based on the API key from cloud-flare on the cert-manager namespace.
- Create a CluterIssuer resource with the secret referenced. This kind of resource allows us to use it throughout the cluster regardless of the namespace.
- For testing purpose, we can create a the LetsEncrypt Staging endpoint to make sure its working before switching to the production. This is recommended by LE as they *may* block your domain if you set up your environment incorrectly against the production LE endpoint.
REFERENCE: https://cert-manager.io/docs/configuration/acme/dns01/cloudflare/
ClusterIssuer manifest
apiVersion: cert-manager.io/v1alpha2
kind: ClusterIssuer
metadata:
name: letsencrypt-stg
namespace: cert-manager
spec:
acme:
# staging
server: https://acme-staging-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt
solvers:
- dns01:
cloudflare:
email: <YOUR EMAIL>
apiTokenSecretRef:
name: cloudflare-api-token
key: api-token
---
apiVersion: cert-manager.io/v1alpha2
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
namespace: cert-manager
spec:
acme:
# production
server: https://acme-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt
solvers:
- dns01:
cloudflare:
email: <YOUR EMAIL>
apiTokenSecretRef:
name: cloudflare-api-token
key: api-token
Creating the Harbor Certificate
Once we have ClusterIssuer setup, we need to request the certificate for harbor to use.
- Create a namespace where we will install harbor
- Create a certificate resource on the namespace where harbor will be installed. This is because certificate/secret resource are namespaced.
Certificate Request Manifest:
apiVersion: cert-manager.io/v1alpha2
kind: Certificate
metadata:
name: harbor-cert
namespace: harbor
spec:
secretName: harbor-cert
issuerRef:
name: letsencrypt-prod
kind: ClusterIssuer
commonName: <FQDN of the harbor resource>
dnsNames:
- <FQDN of the harbor resource, any additional SAN>
- After creation of the certificate object, wait around 1-2 minutes for the certificate to be request.
- You can get the status of the certificate request by issuing the following
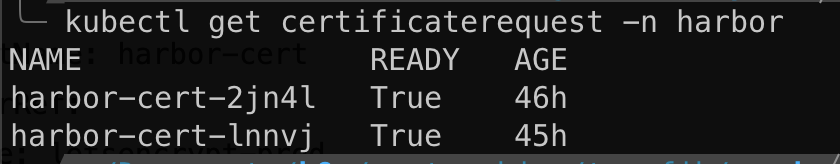
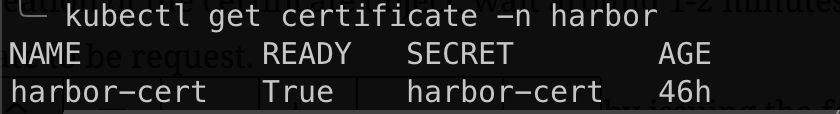
Setting up Traefik
Once we have the issuer ready, now it’s time to setup Traefik as an ingress controller. Documentation to install is fully documented in their website. Personally, I prefer installing the CRD’s and deployments manually. Refernece for the CRD’s to use is documented here: https://doc.traefik.io/traefik/reference/dynamic-configuration/kubernetes-crd/
Set-up entry-points for Notary
In the static configuration of Traefik (I prefer to use configmap), make sure to open up 4443 which is the port Notary needs to expose it’s service. In addition, its also a good time to make sure the proper providers are setup in the static config.
NOTE: We won’t be using the ingressClass as the Certificates will be installed directly to Harbor. Traefik will be configured to passthrough.
Static Config:
providers:
kubernetesCRD: {}
kubernetesIngress:
ingressClass: "traefik-certmanager"
entryPoints:
web:
address: ":80"
web-secure:
address: ":443"
web-4443:
address: ":4443"
admin:
address: ":8080"
Setting up Harbor
Harbor is installed using helm (shame) which is customized by passing in a values.yaml. The complete values definition is included in the github page here: https://github.com/goharbor/harbor-helm/blob/master/values.yaml
For this setup, we would be setting up the values.yaml as follows:
expose:
# we will use clusterIP as Traefik will be fronting our application
type: clusterIP
tls:
enabled: true
certSource: secret
auto:
commonName: ""
secret:
# specify secret resource created by cert-manager in the previous step.
secretName: "harbor-cert"
You can consider modifying the PV as well if you prefer to increase the disk used by harbor. By default, it only creates 5GB of disk.
Once you have the values.yaml customized, install harbor by doing the following:
helm install harbor harbor/harbor -f values.yaml -n harbor
Setting IngressRoutes for Harbor
Once we have Harbor up and running, it’s time to create Traefik’s IngressRoute to expose Harbor to the outside world. We will be exposing three ports: 80, 443, and 4443. Make sure this ports are part of Traefik’s static configuration.
Sample IngressRoutes:
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRouteTCP
metadata:
name: harbor-https
namespace: harbor
spec:
entryPoints:
- web-secure
routes:
- match: HostSNI(`FQDN HERE`)
kind: Rule
services:
- name: harbor
port: 443
tls:
passthrough: true
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRouteTCP
metadata:
name: harbor-4443
namespace: harbor
spec:
entryPoints:
- web-4443
routes:
- match: HostSNI(`FQDN HERE`)
kind: Rule
services:
- name: harbor
port: 4443
tls:
passthrough: true
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: harbor-route-http
namespace: harbor
spec:
entryPoints:
- web
routes:
- match: Host(`FQDN HERE`)
kind: Rule
services:
- name: harbor
port: 80
middleware:
- name: redirect
namespace: traefik
NOTE: For the HTTP resource, I used a middleware to redirect HTTP to HTTPS. This resource is created in the traefik namespace hence the reference. Middleware examples are in the traefik documentations.
Once this is done, your all set and hopefully have harbor up and accessible using the FQDN you specified.
Hope that helps. Enjoy!





Great post, thank you for sharing
Hi,
Really liking the site!
If you require any devops services please get in touch, we’d be honoured to
help you out.
https://shorturl.fm/24zD4
Your writing style is very engaging.
https://shorturl.fm/iocyV
https://shorturl.fm/OTrB0
https://shorturl.fm/AvCQb
https://shorturl.fm/sbrjY
https://shorturl.fm/7BDq6
https://shorturl.fm/oik33
https://shorturl.fm/GOFa5
https://shorturl.fm/kpUvf
https://shorturl.fm/YpHPi
https://shorturl.fm/3Znnz
https://shorturl.fm/KR60c
https://shorturl.fm/0hyvw
https://shorturl.fm/y0yP2
https://shorturl.fm/MNRxs
https://shorturl.fm/Z9Nqo
https://shorturl.fm/eZGbc
https://shorturl.fm/Pm9g6
https://shorturl.fm/V81R5
You made some clear points there. I did a search on the subject and found most people will approve with your site.
https://shorturl.fm/K84Y1
https://shorturl.fm/hXkQI
https://shorturl.fm/1Rrx2
https://shorturl.fm/lilDS
https://shorturl.fm/7bHvB
https://shorturl.fm/Z7Y9g
https://shorturl.fm/wQsON
https://shorturl.fm/dZVvL
https://shorturl.fm/F3N34
https://shorturl.fm/QllcG
https://shorturl.fm/l8kmF
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
https://shorturl.fm/PnPrK
https://shorturl.fm/Eust8
https://shorturl.fm/Qxzkv
https://shorturl.fm/KwX3L
https://shorturl.fm/fjKzC
https://shorturl.fm/5CWtk
https://shorturl.fm/uEUf9
https://shorturl.fm/vUn62
https://shorturl.fm/sAdsS
https://shorturl.fm/TWnnx
order thc softgels discreet delivery
https://shorturl.fm/TuXuB
https://shorturl.fm/1poVx
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis
marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas
que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros
gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de
juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas deportivas
gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas
en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas
sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas
ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre
amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app
casas de apuestas|app control apuestas|app de apuestas|app de apuestas
android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas
deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de
apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app
de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de
apuestas para android|app de apuestas para ganar dinero|app
de apuestas peru|app de apuestas reales|app de casas de
apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para
apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para
hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de
bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de
apuestas mexico|apps para apuestas|aprender a hacer apuestas
deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas
3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a
corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la
baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al
tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas
altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas
america|apuestas android|apuestas anillo nba|apuestas antes del
mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del
mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia
mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises
bajos|apuestas argentina polonia|apuestas argentina
uruguay|apuestas argentina vs australia|apuestas argentina vs
colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas
athletic atletico|apuestas athletic barça|apuestas
athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas
athletic valencia|apuestas atletico|apuestas atletico
barcelona|apuestas atletico barsa|apuestas atletico
campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de
madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de
madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas
atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto
hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça
hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real
madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona
atletico|apuestas barcelona atletico de madrid|apuestas
barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas
barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real
sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis
– chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas
bienvenida|apuestas billar online|apuestas bolivia vs
colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida
sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos
sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de
campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas
boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas
brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos
zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas
campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de
champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de
caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras
caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos
hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras
de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino
madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas
celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas
champions league hoy|apuestas champions league pronosticos|apuestas champions
league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas
chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas
ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city
madrid|apuestas city real madrid|apuestas
clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas
clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas
colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas
futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas
combinadas mundial|apuestas combinadas nba|apuestas combinadas
para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas
pronosticos|apuestas combinadas recomendadas|apuestas combinadas
seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras
para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa
del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey
final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del
rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas
de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas
de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de
boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de
caballos en colombia|apuestas de caballos en españa|apuestas
de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de
caballos pronósticos|apuestas de carrera de
caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de
colombia|apuestas de copa america|apuestas de corners|apuestas de
deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de
eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de
fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol
colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de
futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas
de futbol para hoy|apuestas de fútbol para hoy|apuestas
de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol
pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de
galgos online|apuestas de galgos trucos|apuestas de golf|apuestas
de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas
de juegos online|apuestas de la champions league|apuestas
de la copa américa|apuestas de la eurocopa|apuestas de la
europa league|apuestas de la liga|apuestas de la liga bbva|apuestas
de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas
de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas
ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema
explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis
pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas
de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia
futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas
deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas
deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas
deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de
mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas
combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas
con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos
virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas
deportivas copa america|apuestas deportivas
copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas
de colombia|apuestas deportivas de futbol|apuestas
deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas
deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas
deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas
deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas españa|apuestas
deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula
1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas
francia argentina|apuestas deportivas futbol|apuestas
deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas
gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis
hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas
deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas
interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas
la liga|apuestas deportivas legales|apuestas
deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas
deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas
deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas
mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas
ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas
online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas
deportivas online mexico|apuestas deportivas
online paypal|apuestas deportivas online peru|apuestas deportivas online por
internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas
deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas
deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas
deportivas pronósticos|apuestas deportivas pronosticos
expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos
tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas
resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para
hoy|apuestas deportivas seguras telegram|apuestas deportivas
sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas
sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas
tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas
deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas
tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia
barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas
y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas
deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la
liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas
doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y
triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs
venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de
caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas
en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas
en españa|apuestas en esports|apuestas en eventos deportivos
virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las
vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea
chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea
peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas
en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis en directo|apuestas
en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas
en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas
en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas
equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa
gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa
italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol
betis|apuestas espanyol villarreal|apuestas esport|apuestas
esports|apuestas esports colombia|apuestas esports españa|apuestas esports
fifa|apuestas esports gratis|apuestas esports lol|apuestas esports
peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa
femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga
baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa
league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas
f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito
champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final
champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas
final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa
league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro
nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas
futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas
futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas
galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas
ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas
ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar
liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona
athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la
liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam
de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis
con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas
gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas
handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas
inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas
juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las
vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas
libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas
liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga
de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas
lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas
madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid
barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid
campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid
gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid
sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters
de tenis|apuestas maximo goleador eurocopa|apuestas
maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos
online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas
mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial
ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial
de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial
ganador|apuestas mundial lol|apuestas mundial
moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub
17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas
nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba
para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super
bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online
boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online
ciclismo|apuestas online colombia|apuestas online comparativa|apuestas
online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online
esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas
online mexico|apuestas online mma|apuestas online movil|apuestas
online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online
sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas
over under|apuestas paginas|apuestas pago anticipado|apuestas
paises bajos ecuador|apuestas paises bajos inglaterra|apuestas
países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el
partido de hoy|apuestas para eurocopa|apuestas para europa
league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar
en la ruleta|apuestas para ganar la champions|apuestas
para ganar la eurocopa|apuestas para ganar la europa league|apuestas
para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas
para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para
la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas
partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido
suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas
partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas
peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas
playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff
segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por
internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos
nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por
tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas
que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas
quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas
quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas
real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real
madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas
real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid
manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real
madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid
vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad
athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas
roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas
segunda|apuestas segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras
baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras
futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras
hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas
sevilla atletico de madrid|apuestas sevilla barcelona|apuestas
sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la
liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como
funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas
super rugby|apuestas supercopa españa|apuestas superliga
argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas
tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa
davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas
tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis
roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas
uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc
hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas
us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia
madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas
venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs
real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas
virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas
y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba
apuestas|argentina apuestas|argentina colombia
apuestas|argentina croacia apuestas|argentina francia
apuestas|argentina mexico apuestas|argentina
peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina
vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de
cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca
apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico
de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid
apuestas|barcelona real sociedad apuestas|barcelona sevilla
apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta
de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs
madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base de
datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet
apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis
madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog
apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas
gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de
apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de
bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono
sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa
de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos
casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de
apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida
casa de apuestas|bonos de bienvenida casas
de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos
en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de
apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas
de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia
apuestas|buenas apuestas para hoy|buscador cuotas
apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas
deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas
sistema|calculadora apuestas yankee|calculadora
arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora
de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora
para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas
deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield
apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera
de caballos apuestas juego|carrera de caballos con apuestas|carrera de
galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos
juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos
apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa
apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa
apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de
mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa
de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa
de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de
bienvenida|casa de apuestas bono gratis|casa de apuestas bono por
registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de
mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas
ciclismo|casa de apuestas colombia|casa de
apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de
peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa
de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas
deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas
deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas
online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de
apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas
en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa
inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de
apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso
mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de
apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa
de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas
nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de
apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas
online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de
apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de
apuestas peru online|casa de apuestas por paypal|casa de
apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas
regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas
sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo
de ingreso|casa de apuestas stake|casa de apuestas
tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial
de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas
deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas
apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas
licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas
nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de
apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de
apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de
apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de
apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas
bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras
de caballos|casas de apuestas casino|casas de apuestas
casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por
registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de
apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas
con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores
cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas
con paypal en perú|casas de apuestas con promociones|casas
de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas
de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de
apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de
apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas
de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas
en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de
apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de apuestas
deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas
peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de
apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas
de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de
apuestas española|casas de apuestas españolas|casas
de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas
de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas
de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de
apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas
futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas
de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas
legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas
de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de
apuestas mundial|casas de apuestas mundial baloncesto|casas de
apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas
en colombia|casas de apuestas nuevas en españa|casas de
apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online
argentina|casas de apuestas online colombia|casas de apuestas online
deportivas|casas de apuestas online ecuador|casas de
apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para
ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas promociones|casas
de apuestas que aceptan paypal|casas de apuestas que comparten cuotas|casas de apuestas que dan dinero gratis|casas de apuestas que no
limitan españa|casas de apuestas que operan en españa|casas de apuestas que
reciben paypal|casas de apuestas que te regalan dinero|casas de apuestas
real madrid|casas de apuestas real madrid arsenal|casas de apuestas real madrid liverpool|casas de
apuestas reguladas en españa|casas de apuestas retiradas tenis|casas de apuestas seguras|casas de apuestas
sevilla|casas de apuestas sin deposito|casas
de apuestas sin deposito minimo|casas de apuestas sin licencia|casas
de apuestas sin licencia en españa|casas de
apuestas sin licencia española|casas de apuestas tenis|casas de apuestas tenis de mesa|casas de
apuestas tercera division|casas de apuestas ufc|casas de apuestas uruguay|casas de
apuestas valencia|casas de apuestas venezuela|casas de apuestas
virtuales|casas de apuestas virtuales perú|casas de apuestas y bonos|casas nuevas apuestas|casas nuevas
de apuestas|casino apuestas|casino apuestas bono sin deposito|casino apuestas deportivas|casino apuestas en linea|casino apuestas
online|casino barcelona apuestas|casino barcelona apuestas deportivas|casino casa de apuestas|casino de apuestas|casino de apuestas cerca
de mi|casino de apuestas deportivas|casino de apuestas online|casino de barcelona apuestas|casino de madrid apuestas|casino gran madrid apuestas|casino madrid apuestas|casino madrid apuestas deportivas|casino online apuestas|casino online apuestas deportivas|casino online apuestas reales|casino y apuestas|casino y apuestas online|casinos apuestas|casinos apuestas deportivas|casinos
online apuestas deportivas|casinos y apuestas|celta alaves apuestas|celta
barcelona apuestas|celta real madrid apuestas|champions league apuestas|champions league apuestas deportivas|champions league apuestas ganador|champions league casa de apuestas|champions league pronosticos apuestas|chelsea betis apuestas|chile apuestas|chile vs argentina
apuestas|chile vs bolivia apuestas|ciclismo apuestas|clasico apuestas|claves para ganar apuestas
deportivas|codigo promocional apuestas|código promocional
apuestas|codigo promocional apuestas deportivas|codigo promocional casa de apuestas|codigo promocional de marca apuestas|colombia apuestas|colombia chile apuestas|colombia uruguay apuestas|colombia
vs uruguay apuestas|combinaciones apuestas|combinaciones apuestas deportivas|combinaciones de apuestas deportivas|combinada
4 5 apuestas|combinada apuestas|combinadas apuestas|combinadas apuestas deportivas|combinadas apuestas hoy|como aprender hacer apuestas
deportivas|como apuestas por internet boxeo|como calcular apuestas|como calcular apuestas deportivas|como calcular cuotas apuestas|como
calcular cuotas de apuestas|como calcular el yield en las apuestas|como calcular las apuestas
deportivas|como calcular unidades apuestas|como crear un sistema de apuestas|como crear una
casa de apuestas online|como declarar apuestas deportivas|como declarar dinero de apuestas|como es doble oportunidad apuestas|como es doble oportunidad en apuestas|como es el handicap asiatico en apuestas|como estan las apuestas barca madrid|como estan las apuestas de la nfl|como estan las
apuestas del clasico|como estan las apuestas en la nfl|como estan las apuestas eurocopa|como estan las apuestas nfl|como estan las apuestas para el
clasico|como estan las apuestas para el mundial|como estan las apuestas
para la eurocopa|cómo están las apuestas para la eurocopa|como funciona el handicap en apuestas|como funciona el sistema
de apuestas|como funciona el stake en apuestas|como funciona handicap apuestas|como funciona sistema
en apuestas|como funcionan apuestas multiples|como funcionan las apuestas combinadas|como funcionan las apuestas de boxeo|como funcionan las apuestas de caballos|como funcionan las apuestas
de sistema|como funcionan las apuestas deportivas|como funcionan las
apuestas dobles|como funcionan las apuestas en linea|como funcionan las
apuestas en ufc|como funcionan las apuestas multiples|como funcionan las
apuestas por sistema|como funcionan las apuestas sistema|como funcionan las apuestas ufc|como funcionan las
cuotas de apuestas|como funcionan los handicaps en apuestas|como funcionan los stakes en apuestas|como ganan dinero las casas
de apuestas|como ganar apuestas|como ganar apuestas combinadas|como
ganar apuestas de galgos|como ganar apuestas de
tenis|como ganar apuestas deportivas|cómo ganar apuestas deportivas|como ganar apuestas deportivas seguras|como ganar apuestas deportivas siempre|como ganar apuestas en baloncesto|como ganar apuestas en vivo|como ganar dinero apuestas|como ganar dinero con apuestas|como
ganar dinero con apuestas seguras|como ganar dinero
con las apuestas|como ganar dinero en apuestas|como ganar dinero en apuestas de futbol|como ganar dinero en apuestas deportivas|como ganar dinero
en casas de apuestas|como ganar dinero en las apuestas|como
ganar en apuestas deportivas|como ganar en apuestas virtuales|como ganar en las apuestas deportivas|como
ganar seguro en apuestas deportivas|como hacer apuestas|como
hacer apuestas combinadas|como hacer apuestas combinadas seguras|como hacer apuestas de futbol|como hacer apuestas de futbol seguras|como hacer apuestas de sistema|como
hacer apuestas deportivas|como hacer apuestas deportivas ganadoras|como hacer apuestas deportivas online|como
hacer apuestas deportivas seguras|como hacer apuestas deportivas
y ganar|como hacer apuestas online|como hacer apuestas por internet|como hacer apuestas seguras|como
hacer apuestas seguras de futbol|como hacer buenas apuestas de futbol|como hacer buenas apuestas deportivas|como hacer dinero en apuestas deportivas|como hacer las apuestas deportivas|como
hacer trading apuestas deportivas|como hacer un sistema
de apuestas|como hacer una casa de apuestas|como mejorar en las apuestas
deportivas|como registrarse en una casa de apuestas|como retirar dinero de marca
apuestas|como se calcula el yield en apuestas|como se calcula las apuestas
deportivas|como se calculan las apuestas|como se calculan las apuestas deportivas|como
se calculan las cuotas de apuestas|como se hace apuestas deportivas|como se hacen apuestas deportivas|como se hacen las apuestas|como se hacen las apuestas de futbol|como se hacen las apuestas deportivas|como se juega apuestas
deportivas|como se juega en las apuestas deportivas|como se juega las apuestas de futbol|como se juega las apuestas
deportivas|como se juegan las apuestas de futbol|como se juegan las apuestas deportivas|cómo se pagan las apuestas de
caballos|como se suman las cuotas de las apuestas|como se tributan las apuestas deportivas|como tributan las apuestas|como tributan las apuestas deportivas|como tributan las ganancias en apuestas|como van las apuestas nfl|comparacion cuotas
casas de apuestas|comparación de casas de apuestas|comparador apuestas|comparador
apuestas champions|comparador apuestas deportivas|comparador apuestas futbol|comparador apuestas online|comparador apuestas seguras|comparador
apuestas tenis|comparador bonos apuestas deportivas|comparador casa de apuestas|comparador casas apuestas|comparador
casas de apuestas|comparador casas de apuestas deportivas|comparador cuotas
apuestas|comparador cuotas apuestas deportivas|comparador cuotas casas de apuestas|comparador cuotas de apuestas|comparador de apuestas|comparador de apuestas colombia|comparador de apuestas deportivas|comparador de
apuestas deportivas online|comparador de apuestas online|comparador de apuestas seguras|comparador de casa de apuestas|comparador de casas de apuestas|comparador de cuotas apuestas|comparador
de cuotas apuestas deportivas|comparador de cuotas casas de apuestas|comparador de cuotas de apuestas|comparar apuestas|comparar apuestas deportivas|comparar casas de apuestas|comparar cuotas apuestas|comparar cuotas apuestas deportivas|comparar cuotas casas de
apuestas|comparar cuotas de apuestas|comparativa apuestas deportivas|comparativa apuestas
online|comparativa casa de apuestas|comparativa casas apuestas|comparativa casas de
apuestas|comparativa casas de apuestas online|comparativa cuotas apuestas|comprobar apuestas deportivas|consejo
de apuestas|consejo de apuestas deportivas|consejos
apuestas|consejos apuestas baloncesto|consejos apuestas caballos|consejos apuestas combinadas|consejos apuestas deportivas|consejos apuestas deportivas combinadas|consejos apuestas deportivas
futbol|consejos apuestas deportivas hoy|consejos
apuestas futbol|consejos apuestas futbol hoy|consejos apuestas
hoy|consejos apuestas nba|consejos apuestas nba hoy|consejos apuestas tenis|consejos de apuestas|consejos de apuestas de futbol|consejos de apuestas de futbol para hoy|consejos de apuestas deportivas|consejos de
apuestas deportivas para hoy|consejos de apuestas para hoy|consejos de apuestas.com|consejos
para apuestas|consejos para apuestas de futbol|consejos para apuestas deportivas|consejos para ganar apuestas de futbol|consejos para ganar apuestas deportivas|consejos para hacer apuestas deportivas|consejos para las apuestas deportivas|conversor de
cuotas apuestas|copa africa apuestas|copa america apuestas|copa davis apuestas|copa del rey 2025 apuestas|copa del rey apuestas|copa libertadores
apuestas|copa libertadores apuestas deportivas|copa sudamericana apuestas|corners apuestas|corners
en apuestas|csgo paginas apuestas|csgo paginas de apuestas|cual es el mejor sitio de
apuestas|cual es la casa de apuestas mas segura|cual es la mejor app de apuestas|cual es la mejor
casa de apuestas|cual es la mejor casa de apuestas online|cual
es la mejor pagina de apuestas|cuales son las apuestas mas seguras|cuantas apuestas
hacer al dia|cuantas casas de apuestas hay en españa|cuantas casas de
apuestas hay en madrid|cuanto se paga de impuestos por apuestas|cuanto tributan las apuestas deportivas|cuanto vale una tarjeta roja en apuestas|cuenta la prorroga en las apuestas|cuenta la prórroga en las apuestas|cuota apuestas|cuota apuestas mundial|cuota en apuestas|cuotas altas apuestas deportivas|cuotas
americanas apuestas|cuotas apuestas|cuotas apuestas balonmano|cuotas apuestas champions|cuotas apuestas champions league|cuotas
apuestas copa del rey|cuotas apuestas deportivas|cuotas apuestas eurocopa|cuotas apuestas f1|cuotas apuestas final champions|cuotas apuestas futbol|cuotas apuestas
hoy|cuotas apuestas la liga|cuotas apuestas liga|cuotas apuestas mundial|cuotas apuestas nba|cuotas bajas apuestas|cuotas casas de
apuestas|cuotas de apuestas|cuotas de apuestas de futbol|cuotas de apuestas deportivas|cuotas de futbol apuestas|cuotas de todas las casas de apuestas|cuotas en apuestas|cuotas en apuestas deportivas|cuotas mas altas apuestas deportivas|curso apuestas deportivas
gratis|curso de apuestas deportivas gratis|declarar apuestas deportivas|declarar dinero apuestas|declarar dinero apuestas deportivas|declarar dinero de apuestas|declarar dinero
ganado en apuestas|declarar ingresos por apuestas|declarar perdidas apuestas online|declarar pérdidas
apuestas online|deportes apuestas en vivo|deposito minimo 5 euros apuestas|depósito
mínimo casas de apuestas|diferentes tipos de apuestas deportivas|dinero
apuestas|dinero apuestas declarar|dinero gratis
apuestas|dnb apuestas|dnb apuestas deportivas|dnb apuestas que
es|dnb en apuestas|doble doble apuestas|doble
doble baloncesto apuestas|doble doble nba apuestas|doble
o nada apuestas|doble oportunidad apuestas|doble oportunidad apuestas deportivas|doble
oportunidad apuestas que es|doble oportunidad apuestas significado|doble oportunidad en apuestas|donde hacer apuestas de futbol|donde hacer apuestas deportivas|donde
puedo hacer apuestas deportivas|donde se hacen las apuestas deportivas|el
clasico apuestas|el comparador apuestas|el comparador de apuestas|el mejor analista de
apuestas deportivas|el mejor canal de apuestas
deportivas|el mejor excel para apuestas deportivas|el mejor sitio de apuestas|el mejor sitio de apuestas deportivas|el
mejor sitio de apuestas online|el mejor sitio de apuestas por internet|el mejor
sitio para apuestas|empate no valido apuestas|empresa de apuestas deportivas|empresas
apuestas|empresas apuestas deportivas|empresas de apuestas|empresas de apuestas
deportivas|empresas de apuestas deportivas en peru|empresas de apuestas en españa|empresas
de apuestas online|en apuestas deportivas que significa 1×2|en apuestas que es 1×2|en apuestas que significa
1×2|en apuestas que significa handicap|en apuestas que significa mas de 1.5|en las apuestas cuenta la prorroga|en las apuestas que significa 1×2|en las apuestas que significa handicap|en las apuestas que significa mas de 1.5|errores de cuotas casas de apuestas|es bueno hacer apuestas deportivas|españa – francia apuestas|españa alemania apuestas|españa apuestas|españa apuestas eurocopa|españa casas de apuestas|españa eurocopa apuestas|españa francia apuestas|españa
francia eurocopa apuestas|españa georgia apuestas|españa inglaterra apuestas|españa italia apuestas|españa mundial apuestas|esport apuestas|esports apuestas|estadistica
apuestas deportivas|estadistica en apuestas deportivas|estadistica para apuestas deportivas|estadisticas apuestas|estadísticas apuestas|estadisticas apuestas deportivas|estadísticas apuestas deportivas|estadisticas apuestas deportivas futbol|estadisticas apuestas futbol|estadisticas apuestas hoy|estadisticas apuestas nba|estadisticas
baloncesto apuestas|estadisticas casas de
apuestas|estadisticas de apuestas|estadisticas
de apuestas de futbol|estadisticas de apuestas deportivas|estadísticas de apuestas
deportivas|estadisticas de apuestas futbol|estadisticas
de futbol apuestas|estadisticas de futbol para apuestas|estadisticas deportivas para apuestas|estadísticas deportivas
para apuestas|estadisticas en apuestas deportivas|estadisticas futbol apuestas|estadísticas fútbol apuestas|estadisticas futbol apuestas deportivas|estadisticas futbol para apuestas|estadisticas nba apuestas|estadisticas para apuestas|estadisticas para apuestas de futbol|estadisticas para apuestas deportivas|estadísticas para apuestas deportivas|estadisticas
para apuestas futbol|estadisticas tenis apuestas|estadísticas tenis apuestas|estrategia apuestas|estrategia apuestas baloncesto|estrategia apuestas combinadas|estrategia apuestas corners|estrategia
apuestas deportivas|estrategia apuestas deportivas seguras|estrategia apuestas en vivo|estrategia apuestas resultado exacto|estrategia apuestas tenis|estrategia apuestas
tenis de mesa|estrategia corners apuestas|estrategia de apuestas|estrategia de apuestas deportivas|estrategia empates
apuestas deportivas|estrategia ganadora apuestas deportivas|estrategia tenis de
mesa apuestas|estrategias apuestas|estrategias apuestas de futbol|estrategias
apuestas deportivas|estrategias apuestas deportivas futbol|estrategias apuestas
en vivo|estrategias apuestas futbol|estrategias apuestas tenis|estrategias de
apuestas|estrategias de apuestas de futbol|estrategias de apuestas deportivas|estrategias de apuestas deportivas
pdf|estrategias de apuestas futbol|estrategias de
apuestas seguras|estrategias para apuestas de futbol|estrategias para apuestas deportivas|estrategias tenis apuestas|eurocopa apuestas|eurocopa apuestas campeon|eurocopa apuestas ganador|eurocopa casas de apuestas|eurocopa favoritos apuestas|eurocopa femenina apuestas|eurocopa ganador apuestas|europa
league apuestas|evolucion cuotas apuestas|excel para apuestas deportivas
gratis|explicacion handicap apuestas|explicacion stake apuestas|f1 apuestas|favorito apuestas champions|favorito champions
apuestas|favorito en las apuestas super bowl|favoritos apuestas champions
league|favoritos apuestas eurocopa|favoritos apuestas mundial|favoritos casas de apuestas champions|favoritos champions apuestas|favoritos champions casas de apuestas|favoritos eurocopa
apuestas|favoritos mundial apuestas|favoritos mundial casas de
apuestas|favoritos mundial qatar apuestas|favoritos
nba apuestas|favoritos papa apuestas|fc barcelona apuestas|final champions league apuestas|final
copa america apuestas|final copa del rey apuestas|final eurocopa apuestas|final europa league apuestas|final mundial apuestas|final nba apuestas|formula 1 apuestas|formula apuestas deportivas|fórmula excel para apuestas deportivas|formula matematica apuestas deportivas|fórmula matemática apuestas deportivas|formula para ganar apuestas deportivas|fórmula para ganar apuestas deportivas|fórmulas para ganar
apuestas deportivas|foro apuestas|foro apuestas acb|foro apuestas baloncesto|foro apuestas balonmano|foro apuestas beisbol|foro apuestas caballos|foro apuestas ciclismo|foro
apuestas de tenis|foro apuestas deportivas|foro apuestas deportivas baloncesto|foro apuestas deportivas futbol|foro apuestas deportivas futbol español|foro apuestas deportivas nba|foro apuestas deportivas tenis|foro apuestas futbol|foro apuestas futbol español|foro apuestas
mlb|foro apuestas mundial|foro apuestas nba|foro apuestas
tenis|foro casas de apuestas|foro de apuestas|foro de apuestas combinadas|foro de apuestas de futbol|foro de apuestas de tenis|foro de apuestas deportivas|foro de apuestas deportivas futbol|foro de apuestas deportivas tenis|foro de apuestas futbol|foro de apuestas nba|foro nba apuestas|foro pronosticos apuestas|foro sobre apuestas deportivas|foro tenis apuestas|foro tenis apuestas deportivas|foros apuestas deportivas|foros apuestas
tenis|foros de apuestas|foros de apuestas de futbol|foros de
apuestas deportivas|francia argentina apuestas|futbol apuestas|fútbol apuestas|futbol apuestas deportivas|futbol
apuestas pronosticos|futbol español apuestas|futbol hoy apuestas|futbol
virtual apuestas|futbolista sevilla apuestas|galgos apuestas|galgos apuestas deportivas|galgos carreras apuestas|ganador champions league apuestas|ganador copa del rey apuestas|ganador eurocopa apuestas|ganador europa league apuestas|ganador mundial apuestas|ganador
nba apuestas|ganador sin empate apuestas|ganancias apuestas deportivas tributan|ganar 10 euros
al día apuestas|ganar 100 euros al día en apuestas|ganar 50 euros al dia en apuestas|ganar 50 euros al
día en apuestas|ganar apuestas combinadas|ganar apuestas deportivas|ganar apuestas deportivas seguras|ganar apuestas deportivas tenis|ganar
apuestas deportivas trucos|ganar apuestas en vivo|ganar dinero apuestas|ganar dinero apuestas deportivas|ganar dinero apuestas deportivas seguras|ganar dinero con apuestas|ganar dinero
con apuestas deportivas|ganar dinero con apuestas seguras|gente que
vive de las apuestas|gg que significa en apuestas|girona apuestas|girona campeon de liga
apuestas|girona gana la liga apuestas|goles asiaticos apuestas|goles asiaticos en apuestas|grupo de apuestas deportivas gratis|grupos de apuestas gratis|hacer apuestas|hacer apuestas combinadas|hacer apuestas de futbol|hacer apuestas deportivas|hacer
apuestas online|hacer apuestas seguras|hacer dinero con apuestas deportivas|handicap apuestas|hándicap apuestas|handicap
apuestas baloncesto|hándicap apuestas baloncesto|handicap apuestas basket|handicap apuestas beisbol|handicap apuestas deportivas|handicap apuestas futbol|handicap apuestas futbol
explicacion|handicap apuestas nba|handicap apuestas nfl|handicap apuestas que es|handicap apuestas significado|handicap apuestas tenis|handicap asiatico apuestas|handicap asiatico en apuestas|handicap baloncesto apuestas|handicap en apuestas|handicap en apuestas baloncesto|handicap
en apuestas de baloncesto|handicap en apuestas deportivas|handicap en apuestas que es|handicap en apuestas que significa|handicap en las
apuestas|handicap que es apuestas|hándicap que es apuestas|handicap que es en apuestas|handicap que significa apuestas|handicap que
significa en las apuestas|handicap significado apuestas|hándicap significado en apuestas|hay gente que
vive de las apuestas|historico cuotas apuestas|histórico cuotas apuestas|hoja
de calculo apuestas deportivas|hoja de calculo para apuestas deportivas|horario casas de apuestas madrid|impuesto a las
apuestas|impuesto a las apuestas deportivas|impuesto apuestas deportivas|impuesto apuestas online|impuesto de apuestas|impuesto de apuestas deportivas|impuesto por apuestas deportivas|impuesto sobre apuestas|impuestos a las apuestas deportivas|impuestos
a las casas de apuestas|impuestos apuestas|impuestos apuestas deportivas|impuestos apuestas deportivas colombia|impuestos apuestas deportivas españa|impuestos apuestas españa|impuestos apuestas online|impuestos casas de apuestas|impuestos de apuestas|impuestos de apuestas deportivas|impuestos en apuestas|impuestos en apuestas deportivas|impuestos en apuestas deportivas mexico|impuestos ganancias apuestas|impuestos ganancias apuestas deportivas|impuestos por apuestas|impuestos por apuestas deportivas|impuestos por ganancias de apuestas|impuestos sobre apuestas|impuestos sobre apuestas deportivas|indice de tarjetas apuestas|inglaterra paises bajos apuestas|ingreso minimo 5 euros apuestas|ingreso minimo
casas de apuestas|ingresos por apuestas|inter barca apuestas|inter barcelona apuestas|juego apuestas|juego apuestas deportivas|juego apuestas deportivas gratis|juego apuestas futbol|juego apuestas gratis|juego de apuestas|juego de apuestas dinero real|juego de
apuestas futbol|juego de apuestas online|juego de apuestas sin dinero|juego en linea
apuestas|juego online apuestas|juegos apuestas|juegos
apuestas en linea|juegos apuestas online|juegos apuestas
online gratis|juegos con apuestas|juegos con apuestas reales|juegos de apuestas|juegos de apuestas caballos|juegos de apuestas con cartas españolas|juegos de apuestas con dinero real|juegos de
apuestas de caballos|juegos de apuestas de futbol|juegos de
apuestas deportivas|juegos de apuestas deportivas
gratis|juegos de apuestas dinero real|juegos de apuestas en linea|juegos
de apuestas en linea gratis|juegos de apuestas gratis|juegos de apuestas
gratis con premios|juegos de apuestas online|juegos de apuestas online chile|juegos de apuestas online gratis|juegos de apuestas para ganar dinero|juegos de apuestas
sin dinero real|juegos de futbol apuestas|juegos en linea apuestas|juegos
en línea apuestas|juegos en linea de apuestas|juegos olimpicos apuestas|juegos
online apuestas|juegos online de apuestas reales|juegos virtuales
apuestas|juegos y apuestas|juegos y apuestas online|jugador de
sevilla apuestas|jugador del sevilla apuestas|jugador del sevilla apuestas deportivas|jugador sevilla apuestas|jugador sevilla apuestas deportivas|king’s league americas apuestas|la casa de apuestas con mejores cuotas|la casa de
apuestas del real madrid|la liga apuestas|la mejor app de apuestas|la mejor app de apuestas deportivas|la mejor app para apuestas deportivas|la mejor casa de apuestas|la mejor casa de apuestas de españa|la mejor
casa de apuestas deportivas|la mejor casa de apuestas
en colombia|la mejor casa de apuestas en españa|la mejor casa de apuestas en mexico|la mejor casa de
apuestas online|la mejor ia para apuestas deportivas|la mejor pagina
de apuestas|la mejor pagina de apuestas deportivas|la prorroga cuenta en las apuestas|la prórroga cuenta en las
apuestas|la prorroga entra en las apuestas|las apuestas cuentan en la prorroga|las apuestas
deportivas pagan impuestos|las apuestas deportivas son legales|las apuestas incluye
prorroga|las apuestas mas seguras|las apuestas pagan impuestos|las apuestas
valen en la prorroga|las casas de apuestas amañan partidos|las casas de apuestas en españa|las casas de apuestas
pagan impuestos|las ganancias de apuestas tributan|las
mejores app de apuestas|las mejores app de apuestas deportivas|las mejores apuestas deportivas|las mejores
apuestas deportivas para hoy|las mejores apuestas para hoy|las mejores casa
de apuestas peru|las mejores casas de apuestas|las mejores
casas de apuestas de españa|las mejores casas de apuestas deportivas|las mejores casas de apuestas en españa|las
mejores casas de apuestas en peru|las mejores casas de apuestas en perú|las mejores casas de apuestas españa|las mejores casas de apuestas online|las mejores casas de
apuestas peru|las mejores paginas de apuestas|las mejores peñas de apuestas|las prorrogas cuentan en las
apuestas|las tarjetas rojas apuestas|las vegas apuestas mlb|las vegas apuestas nba|legislacion casas de
apuestas españa|ley de juegos y apuestas|licencia apuestas online|licencias apuestas españa|licencias casas de apuestas|liga española apuestas|linea asiatica apuestas|linea de apuestas deportivas|linea de apuestas mlb|linea de apuestas nfl|linea
de apuestas super bowl|linea de dinero apuestas|linea
de dinero en apuestas|linea de gol 3.0 apuestas|linea de
gol apuestas|línea de gol apuestas|linea de gol apuestas
que es|linea de gol apuestas que significa|linea de
gol en apuestas|linea nfl apuestas|lineas asiaticas
apuestas|lineas asiaticas apuestas deportivas|lineas de apuestas mlb|líneas nfl apuestas|lista casas apuestas|lista casas de apuestas españa|lista de apuestas deportivas|lista de casas de apuestas|lista de casas de apuestas deportivas|listado
apuestas|listado apuestas deportivas|listado apuestas deportivas clasico|listado apuestas deportivas prediccion|listado casas apuestas|listado casas de apuestas|listado casas de apuestas españa|listado de apuestas|listado de apuestas deportivas|listado de
casas de apuestas|listado pronosticos apuestas deportivas|lol
esports apuestas|los mejores sitios de apuestas|los mejores tips de apuestas|madrid apuestas|madrid arsenal
apuestas|madrid atletico apuestas|madrid barca apuestas|madrid barça apuestas|madrid barcelona apuestas|madrid barsa apuestas|madrid sevilla
apuestas|madrid vs barcelona apuestas|mapa casas de apuestas madrid|marca apuestas 20 euros gratis|marca apuestas app android|marca apuestas bono|marca apuestas bono 20 euros|marca apuestas
bono bienvenida|marca apuestas codigo promocional|marca apuestas código
promocional|mejor analista de apuestas deportivas|mejor aplicacion apuestas deportivas|mejor aplicación de apuestas
deportivas|mejor app apuestas|mejor app apuestas
deportivas|mejor app apuestas deportivas android|mejor app apuestas deportivas españa|mejor app apuestas futbol|mejor app casa de apuestas|mejor app de apuestas|mejor app de apuestas deportivas|mejor app de apuestas deportivas españa|mejor app de apuestas españa|mejor app de apuestas mexico|mejor app para apuestas|mejor app para apuestas de futbol|mejor app para apuestas deportivas|mejor apuestas|mejor apuestas deportivas|mejor asesor de
apuestas deportivas|mejor bono bienvenida apuestas|mejor bono bienvenida casa apuestas|mejor canal de apuestas deportivas|mejor casa apuestas|mejor casa apuestas deportivas|mejor casa apuestas deportivas
españa|mejor casa apuestas tenis|mejor casa de apuestas|mejor casa de apuestas argentina|mejor casa
de apuestas baloncesto|mejor casa de apuestas
chile|mejor casa de apuestas colombia|mejor casa
de apuestas de españa|mejor casa de apuestas deportivas|mejor casa de apuestas
deportivas españa|mejor casa de apuestas deportivas foro|mejor
casa de apuestas deportivas online|mejor casa
de apuestas deportivas peru|mejor casa de apuestas
en chile|mejor casa de apuestas en colombia|mejor casa de apuestas
en españa|mejor casa de apuestas en linea|mejor casa
de apuestas en mexico|mejor casa de apuestas en méxico|mejor casa de apuestas
en peru|mejor casa de apuestas españa|mejor casa de apuestas esports|mejor casa
de apuestas foro|mejor casa de apuestas futbol|mejor casa de apuestas mexico|mejor casa de apuestas nba|mejor casa de apuestas online|mejor casa de apuestas online españa|mejor casa de apuestas online mexico|mejor casa de apuestas para baloncesto|mejor casa de
apuestas para esports|mejor casa de apuestas para nba|mejor casa de apuestas para tenis|mejor casa de apuestas para ufc|mejor casa de
apuestas perú|mejor casa de apuestas tenis|mejor casas de
apuestas|mejor estrategia apuestas deportivas|mejor estrategia apuestas futbol|mejor foro apuestas de|mejor
grupo de apuestas deportivas|mejor juego de apuestas|mejor juego
de apuestas online|mejor lugar de apuestas deportivas|mejor metodo
de apuestas deportivas|mejor pagina apuestas|mejor pagina apuestas deportivas|mejor página apuestas
deportivas|mejor pagina apuestas futbol|mejor pagina de apuestas|mejor página de apuestas|mejor
pagina de apuestas csgo|mejor pagina de apuestas de futbol|mejor pagina de apuestas deportivas|mejor pagina de apuestas
online|mejor pagina para apuestas deportivas|mejor plataforma de apuestas|mejor plataforma
de apuestas deportivas|mejor pronosticador de apuestas|mejor sitio apuestas|mejor
sitio apuestas deportivas|mejor sitio de apuestas|mejor sitio de apuestas de futbol|mejor sitio de apuestas deportivas|mejor sitio de apuestas online|mejor sitio para apuestas deportivas|mejores app apuestas
deportivas|mejores app de apuestas|mejores app de apuestas
deportivas|mejores apps apuestas|mejores apps apuestas deportivas|mejores apps de
apuestas deportivas|mejores apps de apuestas mexico|mejores apuestas|mejores apuestas champions
league|mejores apuestas combinadas|mejores apuestas combinadas para hoy|mejores apuestas del dia|mejores apuestas deportivas|mejores apuestas europa league|mejores apuestas formula 1|mejores
apuestas nba|mejores apuestas nba hoy|mejores apuestas para
hoy|mejores apuestas para hoy nba|mejores apuestas ruleta|mejores bonos apuestas|mejores bonos apuestas
deportivas|mejores bonos casas de apuestas|mejores bonos de
apuestas|mejores bonos de bienvenida apuestas|mejores bonos de
casas de apuestas|mejores canales de apuestas telegram|mejores
canales telegram apuestas|mejores casa de apuestas|mejores casa de apuestas colombia|mejores casa de apuestas deportivas|mejores casa de apuestas en españa|mejores casa de apuestas españa|mejores casa de apuestas mexico|mejores casa de apuestas online|mejores casas apuestas|mejores casas apuestas españa|mejores casas
apuestas tenis|mejores casas de apuestas|mejores
casas de apuestas argentina|mejores casas de apuestas caballos|mejores casas de apuestas chile|mejores casas de apuestas colombia|mejores casas de apuestas de españa|mejores casas de apuestas deportivas|mejores casas de apuestas en argentina|mejores casas de
apuestas en chile|mejores casas de apuestas en colombia|mejores casas de apuestas en españa|mejores
casas de apuestas en mexico|mejores casas de apuestas en méxico|mejores casas de
apuestas en peru|mejores casas de apuestas españa|mejores casas
de apuestas españolas|mejores casas de apuestas esports|mejores casas de apuestas formula 1|mejores casas de apuestas futbol|mejores casas de apuestas mexico|mejores
casas de apuestas méxico|mejores casas de apuestas nba|mejores casas de apuestas nuevas|mejores casas de apuestas
online|mejores casas de apuestas online españa|mejores casas
de apuestas para tenis|mejores casas de apuestas peru|mejores
casas de apuestas perú|mejores casas de apuestas sin licencia|mejores
casas de apuestas super deporte|mejores casas de apuestas
superdeporte|mejores casas de apuestas tenis|mejores casinos de apuestas deportivas|mejores casinos para apuestas deportivas|mejores combinadas apuestas|mejores consejos de apuestas|mejores cuotas apuestas|mejores
cuotas casas de apuestas|mejores estrategias apuestas
deportivas|mejores ofertas casas apuestas|mejores ofertas casas de apuestas|mejores ofertas de casas de apuestas|mejores paginas apuestas|mejores paginas apuestas csgo|mejores paginas apuestas
de futbol|mejores paginas de apuestas|mejores paginas de apuestas csgo|mejores paginas de
apuestas de futbol|mejores paginas de apuestas deportivas|mejores paginas de apuestas españa|mejores paginas de apuestas mexico|mejores paginas de apuestas online|mejores paginas para apuestas deportivas|mejores plataformas de apuestas|mejores predicciones apuestas|mejores promociones apuestas|mejores promociones apuestas
deportivas|mejores promociones casas apuestas|mejores promociones casas
de apuestas|mejores pronosticos apuestas deportivas|mejores sitios apuestas|mejores sitios de apuestas|mejores sitios de apuestas deportivas|mejores sitios de apuestas mexico|mejores sitios de apuestas
online|mejores tips apuestas deportivas|mejores tipster apuestas
deportivas|mejores tipster de apuestas deportivas|mercados
asiaticos apuestas|mexico apuestas|mis apuestas deportivas|mlb apuestas|mlb apuestas deportivas|mlb
apuestas hoy|mlb apuestas para hoy|momio apuestas|momio en apuestas|momio
significado apuestas|momios apuestas|momios
apuestas nfl|momios apuestas significado|momios en apuestas|multiplicador
de apuestas|mundial 2026 apuestas|mundial apuestas|mundial
ciclismo apuestas|mundial de clubes apuestas|mundial rugby apuestas|mvp nba apuestas|nba apuestas|nba apuestas deportivas|nba apuestas hoy|nba
foro apuestas|nba pronosticos apuestas deportivas|nba spain apuestas|nfl apuestas|nfl apuestas en las vegas|nfl apuestas favoritos|nfl linea de apuestas|nhl apuestas|nueva casa
apuestas|nueva casa de apuestas|nueva casa de apuestas deportivas|nueva
casa de apuestas en colombia|nueva casa de apuestas españa|nueva casas de apuestas|nueva ley apuestas|nueva ley casas de apuestas|nueva ley de apuestas|nueva pagina de apuestas|nuevas apuestas|nuevas apuestas deportivas|nuevas casa de apuestas|nuevas casas apuestas|nuevas casas
apuestas españa|nuevas casas de apuestas|nuevas casas de
apuestas 2025|nuevas casas de apuestas colombia|nuevas casas de apuestas deportivas|nuevas casas
de apuestas en colombia|nuevas casas de apuestas en españa|nuevas
casas de apuestas españa|nuevas casas de apuestas mexico|nuevas casas de apuestas
online|nuevas paginas de apuestas|nuevas paginas de
apuestas csgo|nuevas paginas de apuestas deportivas|nuevo juego de apuestas|nuevos apuestas|numero de casas de apuestas en españa|numero de casas de apuestas en madrid|oferta bienvenida apuestas|oferta casa de apuestas|oferta casas de apuestas|ofertas apuestas|ofertas apuestas deportivas|ofertas apuestas
online|ofertas bienvenida apuestas|ofertas bienvenida casas apuestas|ofertas casa de apuestas|ofertas casas apuestas|ofertas casas de apuestas|ofertas casas
de apuestas deportivas|ofertas de apuestas|ofertas de
apuestas deportivas|ofertas de casas de apuestas|ofertas de empleo apuestas deportivas|ofertas en casas de apuestas|ofertas recurrentes casas de apuestas|ofertas registro casas de apuestas|osasuna real madrid apuestas|over 2.5
apuestas|over apuestas|over en apuestas|over en apuestas deportivas|over en las apuestas|over o under en apuestas|over que es en apuestas|over que significa
en apuestas|over significado apuestas|over under apuestas|over under en apuestas|over y under en apuestas|pagar apuestas con paypal|pagar impuestos por apuestas|pagina apuestas|pagina apuestas csgo|pagina apuestas
deportivas|pagina apuestas españa|pagina apuestas fifa|pagina apuestas
futbol|pagina apuestas gratis|pagina de apuestas|página de apuestas|pagina de apuestas chile|pagina de apuestas colombia|pagina de
apuestas con paypal|pagina de apuestas de csgo|pagina de apuestas de futbol|pagina de apuestas deportivas|página
de apuestas deportivas|pagina de apuestas deportivas chile|pagina de apuestas en venezuela|pagina de apuestas españa|pagina de apuestas esports|pagina de apuestas gratis|pagina de apuestas online|pagina de
apuestas paypal|pagina de apuestas peru|pagina de apuestas por puntos|pagina de apuestas sin dinero|pagina de apuestas stake|pagina para hacer apuestas deportivas|paginas apuestas|páginas apuestas|paginas apuestas csgo|paginas apuestas deportivas|paginas apuestas deportivas chile|paginas apuestas deportivas españa|paginas apuestas españa|paginas apuestas gratis|paginas apuestas nuevas|paginas apuestas online|paginas de
apuestas|páginas de apuestas|paginas de apuestas bono sin deposito|paginas de apuestas casino|paginas de apuestas chile|paginas de apuestas con bono|paginas de apuestas con paypal|paginas de
apuestas cs|paginas de apuestas csgo|paginas de apuestas csgo sin depositar|paginas de apuestas de futbol|paginas de apuestas deportivas|páginas de apuestas deportivas|paginas de apuestas deportivas colombia|paginas de apuestas deportivas en españa|paginas de apuestas
deportivas españolas|paginas de apuestas deportivas gratis|paginas de apuestas deportivas mexico|paginas de apuestas deportivas nuevas|paginas
de apuestas deportivas paypal|paginas de apuestas deportivas peru|paginas
de apuestas en argentina|paginas de apuestas en chile|paginas de
apuestas en colombia|paginas de apuestas en linea|paginas de
apuestas en mexico|paginas de apuestas en venezuela|paginas de apuestas españa|paginas
de apuestas españolas|paginas de apuestas esports|paginas de apuestas mexico|paginas de apuestas nuevas|paginas de apuestas online|paginas de
apuestas paypal|paginas de apuestas peru|paginas de apuestas que aceptan paypal|paginas
de apuestas seguras|paginas de estadisticas para apuestas|paginas de juegos de apuestas|paginas estadisticas apuestas|paginas estadisticas apuestas deportivas|páginas estadísticas para apuestas|paginas para hacer apuestas|paginas para hacer apuestas de futbol|paginas para hacer apuestas deportivas|pago anticipado apuestas|pago anticipado apuestas deportivas|pago anticipado
casa de apuestas|pago anticipado en apuestas|pago impuestos apuestas
deportivas|paises bajos vs ecuador apuestas|para
hacer apuestas|para hacer apuestas deportivas|partido aplazado apuestas|partido suspendido apuestas|partidos amañados apuestas|partidos amañados para apuestas|partidos apuestas hoy|partidos arreglados apuestas|partidos de futbol
hoy apuestas|partidos de fútbol mañana apuestas|partidos de
hoy apuestas|partidos en vivo apuestas|partidos hoy
apuestas|paypal casa de apuestas|paypal casas de apuestas|personas
que viven de las apuestas|peru apuestas|peru chile apuestas|peru vs chile apuestas|peru
vs chile casa de apuestas|plataforma apuestas|plataforma apuestas deportivas|plataforma de apuestas|plataforma de apuestas cruzadas|plataforma de apuestas deportivas|plataforma de apuestas online|plataforma para
apuestas deportivas|plataformas de apuestas|plataformas de apuestas
deportivas|plataformas de apuestas online|plataformas para
apuestas deportivas|prediccion apuestas|prediccion apuestas champions|prediccion apuestas deportivas|prediccion apuestas
deportivas gratis|prediccion apuestas futbol|prediccion apuestas hoy|predicción de apuestas deportivas|prediccion de apuestas futbol|predicciones apuestas|predicciones apuestas baloncesto|predicciones apuestas
champions|predicciones apuestas champions hoy|predicciones apuestas de futbol|predicciones apuestas de tenis|predicciones apuestas deportivas|predicciones apuestas deportivas gratis|predicciones
apuestas deportivas hoy|predicciones apuestas futbol|predicciones apuestas fútbol|predicciones apuestas futbol hoy|predicciones apuestas hoy|predicciones apuestas nba|predicciones apuestas para hoy|predicciones apuestas tenis|predicciones de apuestas|predicciones de apuestas de futbol|predicciones de apuestas deportivas|predicciones de
apuestas para hoy|predicciones de futbol para apuestas|predicciones
futbol apuestas|predicciones para apuestas de futbol|predicciones
para apuestas deportivas|predicciones tenis apuestas|previa apuestas
resultados en vivo|principales casas de apuestas en españa|programa para hacer
apuestas deportivas|promocion apuestas|promocion apuestas deportivas|promocion casa de
apuestas|promociones apuestas|promociones
apuestas deportivas|promociones apuestas gratis|promociones apuestas sin deposito|promociones bienvenida apuestas|promociones casa de apuestas|promociones casas apuestas|promociones casas de apuestas|promociones casas de apuestas deportivas|promociones de apuestas|promociones de apuestas deportivas|promociones de casas de apuestas|promociones en casa de apuestas|promociones en casas
de apuestas|pronosticador apuestas|pronosticador apuestas
futbol|pronosticador de apuestas|pronosticador de apuestas nba|pronosticadores apuestas deportivas|pronosticadores de apuestas|pronostico
apuestas|pronóstico apuestas|pronostico apuestas baloncesto|pronostico apuestas de futbol|pronostico apuestas de futbol para hoy|pronostico apuestas deportivas|pronóstico apuestas deportivas|pronostico apuestas deportivas hoy|pronostico apuestas
europa league|pronostico apuestas futbol|pronostico apuestas futbol hoy|pronostico apuestas hoy|pronostico apuestas hoy futbol|pronostico apuestas la liga|pronostico apuestas nba|pronostico
apuestas nba hoy|pronostico apuestas tenis|pronostico
apuestas tenis hoy|pronostico de apuestas|pronóstico de
apuestas|pronostico de apuestas de futbol|pronostico de apuestas deportivas|pronóstico
de apuestas deportivas|pronostico de apuestas
deportivas hoy|pronóstico de apuestas para hoy|pronostico deportivo apuestas|pronostico
mlb hoy apuestas|pronostico nba hoy apuestas deportivas|pronostico nhl apuestas deportivas|pronostico tenis apuestas
deportivas|pronostico y apuestas nba|pronosticos apuestas|pronósticos apuestas|pronosticos apuestas baloncesto|pronosticos apuestas
beisbol|pronosticos apuestas caballos|pronosticos apuestas ciclismo|pronosticos apuestas combinadas|pronósticos apuestas combinadas|pronósticos apuestas combinadas gratis|pronosticos apuestas combinadas hoy|pronósticos apuestas combinadas
hoy|pronosticos apuestas copa del rey|pronosticos apuestas
de futbol|pronosticos apuestas deportivas|pronósticos apuestas deportivas|pronosticos apuestas deportivas foro|pronosticos apuestas deportivas futbol|pronosticos apuestas deportivas gratis|pronosticos apuestas deportivas hoy|pronosticos apuestas deportivas nba|pronosticos apuestas deportivas tenis|pronósticos apuestas deportivas
tenis|pronosticos apuestas euroliga|pronosticos apuestas euroliga hoy|pronosticos apuestas europa league|pronosticos apuestas europa league
hoy|pronósticos apuestas europa league hoy|pronosticos apuestas formula 1|pronosticos apuestas futbol|pronosticos apuestas
futbol español|pronosticos apuestas futbol hoy|pronosticos apuestas
hoy|pronosticos apuestas liga española|pronósticos apuestas liga española|pronosticos
apuestas nba|pronosticos apuestas nba hoy|pronosticos apuestas
nfl|pronosticos apuestas nhl|pronosticos apuestas premier
league|pronosticos apuestas tenis|pronosticos de apuestas|pronósticos
de apuestas|pronosticos de apuestas de futbol|pronosticos de apuestas de tenis|pronosticos
de apuestas deportivas|pronosticos de apuestas deportivas
hoy|pronosticos de apuestas hoy|pronosticos de apuestas mlb|pronosticos de apuestas
nba|pronosticos de apuestas para hoy|pronosticos deportivo para tus apuestas|pronosticos
deportivos apuestas|pronosticos deportivos para tus apuestas|pronosticos futbol apuestas|pronosticos mlb apuestas deportivas|pronósticos
nfl apuestas deportivas|pronosticos tenis apuestas|pronosticos
y apuestas|pronosticos y apuestas del dia|pronosticos y
apuestas deportivas|prorroga baloncesto apuestas|prorroga en apuestas|proximas casas de apuestas en españa|puntos
de tarjetas apuestas|puntos por tarjetas apuestas|puntos tarjetas apuestas|que app de apuestas
es mejor|que app de apuestas paga mas|que apuestas hacer|que apuestas
hacer hoy|que apuestas puedo hacer|que casa de apuestas aceptan paypal|que casas de apuestas aceptan paypal|que es 1×2 en apuestas|que
es 1×2 en apuestas deportivas|que es asiatico en apuestas|que es asiático en apuestas|que es corners en apuestas|que es dnb apuestas|que es dnb en apuestas|que
es doble doble en apuestas|que es doble oportunidad en apuestas|qué
es doble oportunidad en apuestas|que es doble oportunidad en las apuestas|que
es el 1×2 en apuestas|que es el handicap apuestas|que es el handicap asiatico en apuestas|que es el handicap en apuestas|que es el handicap en apuestas de futbol|que es el
handicap en las apuestas|que es el impuesto a las apuestas|que es el momio en apuestas|que es el momio en las apuestas|que es el over en apuestas|que
es el stake apuestas|que es el stake en apuestas|que es el stake en apuestas deportivas|que es
el stake en las apuestas|que es el total asiatico en apuestas|que es
empate no accion en apuestas|que es ganador sin empate
en apuestas|que es handicap 0 en apuestas|que es handicap apuestas|que
es handicap apuestas baloncesto|que es handicap asiatico en apuestas|que es hándicap asiático
en apuestas|que es handicap asiatico en las apuestas|que es handicap en apuestas|que
es hándicap en apuestas|que es handicap en apuestas baloncesto|que es handicap en apuestas de futbol|que es handicap en apuestas deportivas|que es handicap en las apuestas|qué es handicap en las apuestas|que es handicap
europeo en apuestas|que es la doble oportunidad en apuestas|que es la linea de gol apuestas|que es la linea de gol en apuestas|que es la linea de gol en las apuestas|que es linea de
dinero en apuestas|que es linea de gol apuestas|que es linea de
gol en apuestas|que es linea de gol en las apuestas|que es momio en apuestas|que es over en apuestas|que es over en apuestas deportivas|que es over en las apuestas|que
es over under en apuestas|que es over y under en las apuestas|que es pago anticipado en apuestas|que
es sistema en apuestas|que es stake 1 en apuestas|que es stake 10 en apuestas|que es stake 100 en apuestas|que es stake 2 en apuestas|que es stake 20 en apuestas|que es stake
3 en apuestas|que es stake 30 en apuestas|que es
stake 5 en apuestas|que es stake apuestas|que es stake en apuestas|que es stake en apuestas deportivas|que
es stake en las apuestas|que es tipster en apuestas|que es
total asiatico en apuestas|que es trixie en apuestas|que es
un handicap asiatico en apuestas|que es un handicap en apuestas|que es un momio en apuestas|qué es un momio en las apuestas|que
es un over en apuestas|que es un stake 10 en apuestas|que es
un stake 20 en apuestas|que es un stake apuestas|que es un stake en apuestas|que
es un stake en apuestas deportivas|que es un stake en las apuestas|que es un tipster apuestas|que es un trixie en apuestas|que es un yankee en apuestas|que es una
combinada en apuestas|que es under y over en apuestas|que es yankee en apuestas|que hace un corredor de
apuestas|que quiere decir 1×2 en apuestas|que quiere decir
handicap en apuestas|que quiere decir stake en apuestas|que
significa 0.0 en apuestas|que significa 0.5 en apuestas|que significa 0.5 goles en apuestas|que significa 1 1×2 en apuestas|que significa 1 2 en apuestas|que significa 1 en apuestas|que significa 1.25
en apuestas|que significa 1.5 en apuestas|que significa 1.5 goles
en apuestas|que significa 1/1 en apuestas|que
significa 1/2 en apuestas|que significa 1+ en apuestas|que significa 100 a 1 en apuestas|que significa 12 en apuestas|que significa 1x
en apuestas|que significa 1×2 en apuestas|que significa 1×2 en apuestas 1xbet|que significa 1×2 en apuestas de futbol|que significa 1×2 en apuestas deportivas|que
significa 1×2 en las apuestas|que significa 1×2 g1 en apuestas|que significa 1×2 pa en apuestas|que significa 2.5 en apuestas|que significa 2.5 goles en apuestas|que significa 2+ en apuestas|que significa 2x en apuestas|que
significa 2×1 en apuestas|que significa 3.5 en apuestas|que significa 3.5 goles en apuestas|que
significa 4.5 en apuestas|que significa 4.5 goles en apuestas|que significa 5.5 en apuestas|que significa
ah en apuestas|qué significa apuestas|que significa apuestas con handicap|que significa apuestas sin empate|que significa apuestas sistema|que significa asiatico en apuestas|que
significa asiatico en las apuestas|que significa asiático
en las apuestas|que significa away en apuestas|que significa bankers en apuestas|que significa bts en apuestas|que significa btts en apuestas|que significa cash out en apuestas|que significa corners en apuestas|que significa dnb en apuestas|que significa
dnb en las apuestas|que significa doble chance en apuestas|que significa el
1×2 en apuestas|que significa el 1×2 en las apuestas|que significa el
en las apuestas|que significa el stake en las apuestas|que significa en apuestas 1×2|que significa en apuestas handicap|que significa en las
apuestas 1×2|que significa en las apuestas handicap|que significa handicap 0.0
en apuestas|que significa handicap 1×2 en apuestas|que significa handicap apuestas|que significa handicap en apuestas|que significa handicap en las
apuestas|que significa linea de gol apuestas|que significa linea
de gol en apuestas|que significa más de 2 goles en apuestas|que significa momio
en apuestas|que significa momios en las apuestas|que significa over 0.5 en apuestas|que significa over 1.5 en apuestas|que significa over
2.5 en apuestas|que significa over 4.5 en apuestas|que significa over en apuestas|que significa
over en las apuestas|que significa pa en las apuestas|que significa par e impar en apuestas|que significa sistema en apuestas|que significa stake 1 en apuestas|que significa stake
10 en apuestas|que significa stake 100 en apuestas|que significa stake 2 en apuestas|que significa
stake 20 en apuestas|que significa stake 3 en apuestas|que significa
stake 30 en apuestas|que significa stake 4
en apuestas|que significa stake 5 en apuestas|que
significa stake 50 en apuestas|que significa stake apuestas|que significa stake en apuestas|qué significa stake en apuestas|que significa stake en las
apuestas|que significa tarjetas 1×2 en apuestas|que significa trixie en apuestas|que significa yankee en apuestas|que significan los
stakes en apuestas|que son apuestas combinadas|que son apuestas de sistema|que son apuestas multiples|que son apuestas sistema|que son corners en apuestas|que son las
apuestas asiaticas|que son las apuestas combinadas|que son las apuestas de sistema|que son las
apuestas multiples|que son las apuestas sin empate|que son las apuestas sistema|que son las combinadas en apuestas|que son los asiaticos
en las apuestas|que son los corners en apuestas|que son los handicap en apuestas|que son los handicaps en apuestas|que son los momios en apuestas|que son los momios en las
apuestas|que son los puntos de tarjeta apuestas|que son los
stake en apuestas|que son los stake en las apuestas|que son los stakes en apuestas|que son los stakes en las
apuestas|que son momios en apuestas|que son puntos de tarjetas apuestas|que son stake en apuestas|que son stakes en apuestas|que
tipos de apuestas existen|quien ganara la liga apuestas|ranking
casas de apuestas españa|ranking mejores casas de apuestas|real madrid apuestas|real madrid arsenal apuestas|real madrid atletico apuestas|real
madrid barcelona apuestas|real madrid betis apuestas|real
madrid borussia dortmund apuestas|real madrid casa de apuestas|real
madrid celta apuestas|real madrid hoy apuestas|real madrid osasuna apuestas|real madrid real sociedad apuestas|real madrid sevilla apuestas|real
madrid valencia apuestas|real madrid vs athletic apuestas|real madrid
vs atletico apuestas|real madrid vs atlético madrid
apuestas|real madrid vs barcelona apuestas|real madrid
vs barcelona cuotas apuestas|real madrid vs betis apuestas|real madrid vs celta de vigo apuestas|real madrid vs osasuna apuestas|real madrid vs real sociedad apuestas|real madrid vs sevilla apuestas|real madrid vs valencia apuestas|real madrid vs villarreal
apuestas|real sociedad apuestas|real sociedad barcelona apuestas|real sociedad casa de apuestas|real sociedad casas de apuestas|real sociedad publicidad apuestas|real
sociedad real madrid apuestas|registrarse en apuestas deportivas|registrarse en casa de apuestas|registro de apuestas deportivas|reglas apuestas baloncesto|resultado apuestas|resultado apuestas deportivas|resultado
de apuestas|resultado de apuestas de futbol|resultado
de apuestas de fútbol|resultado de apuestas deportivas|resultado exacto apuestas|resultado final apuestas|resultado final en apuestas|resultados apuestas|resultados
apuestas deportivas|resultados apuestas deportivas futbol|resultados apuestas futbol|resultados de
apuestas|resultados de apuestas de futbol|resultados de apuestas deportivas|resultados de apuestas en vivo|resultados de apuestas gana|resultados de apuestas la perla|resultados futbol apuestas deportivas|resultados para apuestas deportivas|retirada en tenis apuestas|retiradas tenis apuestas|retiradas
tenis casas de apuestas|roll over apuestas|roma athletic apuestas|rugby apuestas|se pagan impuestos por apuestas|segunda division apuestas|sevilla
apuestas|sevilla apuestas jugador|sevilla betis apuestas|sevilla fc apuestas|sevilla inter apuestas|sevilla jugador apuestas|sevilla leganes apuestas|sevilla vs manchester united apuestas|significado 1×2 apuestas|significado de 1×2 en apuestas|significado
de stake en apuestas|significado dnb apuestas|significado linea de gol apuestas|significado over under apuestas|significado over/under apuestas|significado stake apuestas|significado stake en apuestas|simulador de apuestas deportivas|simulador de apuestas deportivas
gratis|sistema 2 3 apuestas|sistema 2 4 apuestas|sistema 2/3 apuestas|sistema 2/4 apuestas|sistema 3 4 apuestas|sistema 3/4 apuestas|sistema apuestas deportivas|sistema de apuestas|sistema de apuestas de futbol|sistema de apuestas
deportivas|sistema de apuestas fibonacci|sistema en apuestas deportivas|sistema
fibonacci apuestas deportivas|sistema ganador apuestas deportivas|sistema martingala apuestas deportivas|sistema para apuestas deportivas|sistema para ganar apuestas deportivas|sistemas de apuestas|sistemas de apuestas combinadas|sistemas de apuestas futbol|sistemas
de apuestas rentables|sistemas para apuestas deportivas|sitio apuestas|sitio apuestas deportivas|sitio de apuestas|sitio de apuestas
argentina|sitio de apuestas de futbol|sitio de apuestas de fútbol|sitio de apuestas deportivas|sitio de apuestas deportivas argentina|sitio de apuestas futbol|sitio de
apuestas gratis|sitio de apuestas online|sitio de apuestas
peru|sitios apuestas|sitios apuestas deportivas|sitios apuestas online|sitios de apuestas|sitios de apuestas
argentina|sitios de apuestas con bono sin deposito|sitios
de apuestas de dota 2|sitios de apuestas de futbol|sitios de
apuestas deportivas|sitios de apuestas deportivas argentina|sitios de apuestas deportivas online|sitios de apuestas deportivas peru|sitios
de apuestas en argentina|sitios de apuestas en linea|sitios de apuestas en mexico|sitios de apuestas gratis|sitios de apuestas mexico|sitios de apuestas online|sitios de apuestas peru|sitios de apuestas por internet mexico – Diepantech.com.vn,|sitios de apuestas que aceptan paypal|sitios para
apuestas deportivas|sitios web de apuestas|software estadístico apuestas deportivas|software prediccion apuestas deportivas|software predicción apuestas deportivas|son legales las
apuestas deportivas|sport apuestas tipster|spread en español
apuestas|stake 1 apuestas|stake 1 en apuestas|stake
10 apuestas|stake 10 en apuestas|stake 2 apuestas|stake 3 apuestas|stake 5 apuestas|stake 5 en apuestas|stake apuestas|stake apuestas app|stake apuestas colombia|stake apuestas deportivas|stake apuestas españa|stake apuestas que es|stake apuestas que significa|stake apuestas significado|stake casa de
apuestas|stake en apuestas|stake en apuestas deportivas|stake
en apuestas que es|stake en apuestas que significa|stake en apuestas significado|stake en las
apuestas|stake que es apuestas|stake que es en apuestas|stake significado
apuestas|stakes apuestas|stakes en apuestas|super yankee apuestas|superdeporte mejores
casas de apuestas|tabla apuestas múltiples|tabla stake apuestas|tarjeta roja en apuestas|tarjeta roja vale por
dos en apuestas|tarjetas amarillas apuestas|tarjetas amarillas en apuestas|tarjetas
apuestas|tarjetas apuestas deportivas|tarjetas en apuestas|tarjetas en apuestas deportivas|tenis apuestas|tenis apuestas deportivas|tenis de mesa apuestas|tip apuestas|tipo de apuestas|tipo
de apuestas deportivas|tipo de apuestas entre amigos|tipos apuestas|tipos de apuestas|tipos de apuestas betplay|tipos de
apuestas carreras de caballos|tipos de apuestas combinadas|tipos de apuestas de caballos|tipos de
apuestas de futbol|tipos de apuestas deportivas|tipos de apuestas en baloncesto|tipos de apuestas en caballos|tipos de apuestas en futbol|tipos de apuestas
en la ruleta|tipos de apuestas entre amigos|tipos de apuestas futbol|tipos de apuestas hipicas|tipos de apuestas hipodromo|tipos de
apuestas online|tipos de casas de apuestas|tipos de cuotas apuestas|tipos de handicap apuestas|tipos de juegos de apuestas|tips
apuestas|tips apuestas deportivas|tips apuestas deportivas gratis|tips apuestas deportivas hoy|tips
apuestas futbol|tips apuestas gratis|tips apuestas hoy|tips apuestas nba|tips apuestas nfl|tips apuestas tenis|tips de apuestas|tips
de apuestas de futbol|tips de apuestas deportivas|tips de apuestas para hoy|tips
deportivos apuestas|tips gratis apuestas|tips para apuestas|tips para apuestas de futbol|tips para apuestas deportivas|tips para ganar apuestas deportivas|tips
para ganar en apuestas deportivas|tips tenis apuestas|tipster apuestas|tipster apuestas combinadas|tipster apuestas deportivas|tipster apuestas deportivas gratis|tipster apuestas futbol|tipster apuestas
gratis|tipster apuestas hoy|tipster apuestas tenis|tipster de apuestas|tipster de apuestas deportivas|todas las
casas de apuestas|todas las casas de apuestas de españa|todas las casas de apuestas
en españa|todas las casas de apuestas españa|top casas de apuestas españa|top casas de apuestas peru|total asiatico en apuestas|total tarjetas apuestas|tributación apuestas deportivas|tributar apuestas
deportivas|tributar ganancias apuestas deportivas|trixie 4
apuestas|trixie apuestas|truco apuestas|truco apuestas combinadas|truco apuestas deportivas|truco
apuestas seguras|truco para ganar en apuestas deportivas|trucos
apuestas|trucos apuestas carreras de caballos|trucos apuestas
de futbol|trucos apuestas deportivas|trucos apuestas deportivas futbol|trucos apuestas futbol|trucos apuestas galgos|trucos casas de apuestas|trucos de apuestas|trucos de apuestas deportivas|trucos en apuestas deportivas|trucos ganar apuestas deportivas|trucos para apuestas|trucos para apuestas deportivas|trucos para ganar apuestas|trucos para ganar
apuestas de futbol|trucos para ganar apuestas deportivas|trucos para ganar en apuestas de futbol|trucos
para ganar en las apuestas|trucos para hacer apuestas deportivas|trucos para las apuestas deportivas|uefa champions
league apuestas|uefa europa league apuestas|ufc apuestas|ufc
apuestas hoy|ufc apuestas por internet|ufc hoy apuestas|under over apuestas|under y over
en apuestas|uruguay apuestas|uruguay apuestas deportivas|uruguay vs colombia apuestas|vale la prorroga en las apuestas|valencia athletic apuestas|valencia
barcelona apuestas|valencia getafe apuestas|valencia madrid apuestas|valencia real madrid apuestas|valencia vs barcelona apuestas|valencia vs
real madrid apuestas|venezuela apuestas|venezuela argentina apuestas|venezuela vs bolivia apuestas|villarreal apuestas|villarreal liverpool apuestas|vive
de las apuestas|vive de las apuestas deportivas|vive la suerte
apuestas|vive la suerte apuestas deportivas|vivir de las apuestas deportivas|vivo de las apuestas|vivo de las apuestas deportivas|walkover
tenis apuestas|web apuestas casino no dep bono|yankee apuestas)
Enter your invite code to earn your airdrop on Aster https://is.gd/ZceEI6
Share your unique link and earn up to 40% commission!
Share our products, earn up to 40% per sale—apply today!
Invite your network, boost your income—sign up for our affiliate program now!
Unlock exclusive rewards with every referral—apply to our affiliate program now!
Share your unique link and earn up to 40% commission!
That is really fascinating, You’re a very skilled blogger.
I’ve joined your feed and look forward to in the hunt
for extra of your excellent post. Also, I have shared your website in my social networks
**boostaro**
Boostaro is a purpose-built wellness formula created for men who want to strengthen vitality, confidence, and everyday performance.
**neurosharp**
Neuro Sharp is an advanced cognitive support formula designed to help you stay mentally sharp, focused, and confident throughout your day.
Promote our products and earn real money—apply today!
Boost your earnings effortlessly—become our affiliate!